This page describes how to retrieve a lost wireless key. This process more describes my success with the a widely excepted method. I pretty much followed this method through. Visit Aricrack-ng Simple WEP Crack for a guide.
My Setup
- Dell Inspiron 530
- Mint Linux 6 (an Adaption of Ubuntu 8.10)
- Aircrack-ng 1.0 rc1 – (C) 2006,2007,2008 Thomas d’Otreppe (From Ubuntu Repos)
- Linksys (Cisco) Wireless WUSB54Gv4
- 2 rolled up copies of the Evening Standard, to allow the antenna into freespace away from the building a little
The antenna setup is shown below:
- The antenna element, typically vertically polarised
- The network card, Linksys WUSB54Gv4
- The newspapers
What Happened
By following the instructions on this page, I was able to retrieve the key for my example. It should be noted here that after I put the WUSB54Gv4 into monitor mode, using airmon-ng it created a virtual device, mon0. I referred tho this device and not wlan0. This method worked fine. I followed the tutorial completely, and collected around 4million IVs. Computing of the actual key with aircrack-ng too in the region of 5 seconds, although reading in 1.7GBy of data took around 1 minute.
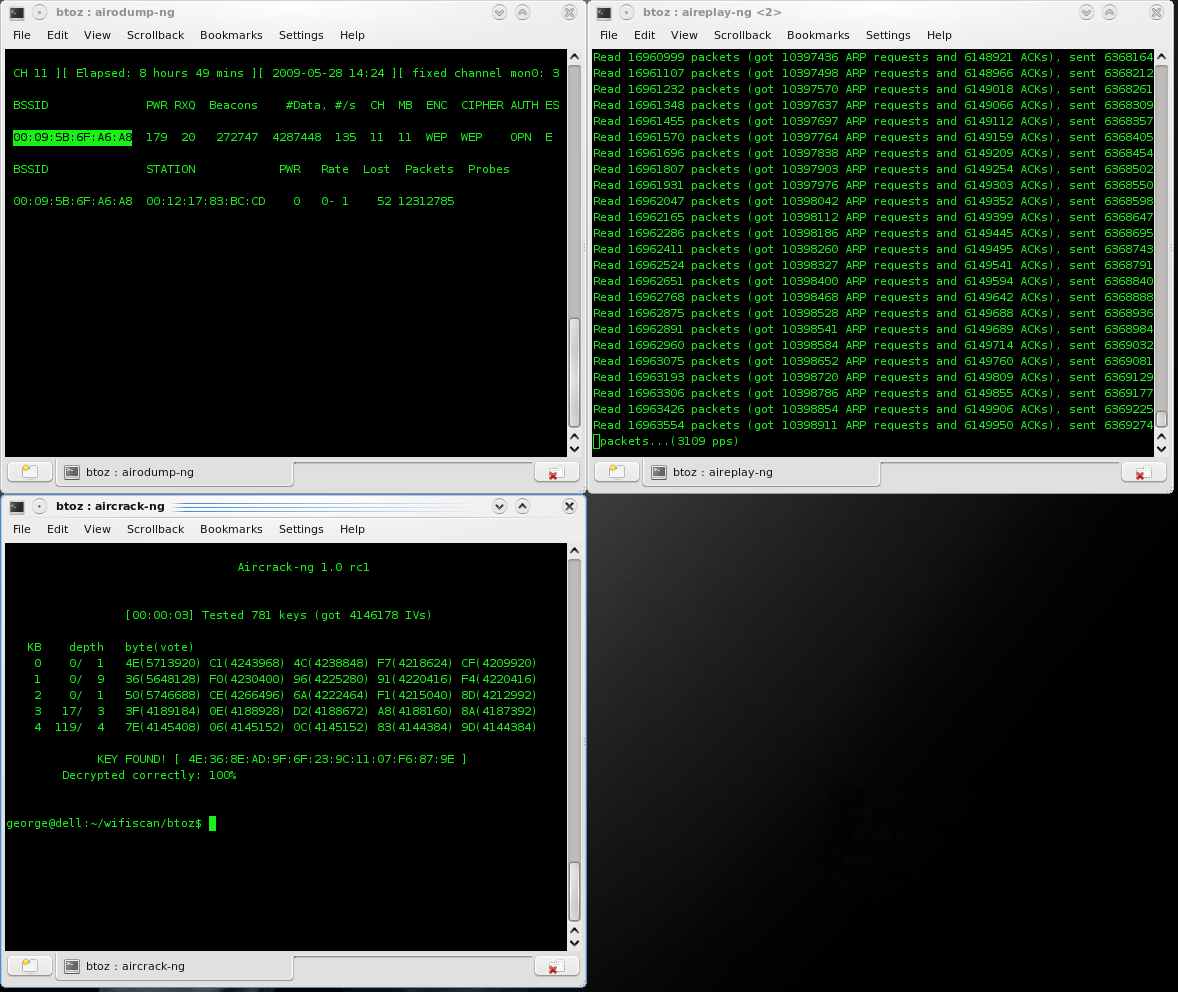
The image below shows the terminal windows doing the work:
- Top/Left: airodump-ng saves the IV’s (Initialisation Vectors) to the harddisk, as a .cap file.
- Top/Right: aireplay-ng collects ARP requests, and then resends them back into the network, generating more IVs and encrypted data.
- Bottom/Left: aircrack-ng reads the .cap files, and computes the key using ‘clever algorithms’.
- Bottom/Right: A section of my desktop wallpaper showing though 🙂